- Why Us?
- Features
White Label
For SaaS Platforms & Agencies
Provide our complete analytics suite to your clients, directly within your own interface and with your/their own branding. Discover Analytics-as-a-Service and White Label Analytics. Great benefit, minimal effort.
- Pricing
- White Label
- Success Stories
- ResourcesGetting Started
Apple Boosts Data Security to Thwart Hackers

Apple is giving consumers, who may be at risk from highly targeted cyberattacks by commercial businesses creating state-sponsored mercenary spyware, specific additional protection through a ground-breaking security feature that is now under preview.
The tech giant is also disclosing information on a $10 million grant it received to support research uncovering these vulnerabilities.
Apple declared on December, 7 that it will soon provide customers with the option to encrypt more of the data that is backed up to their iCloud using end-to-end encryption, making it impossible for anybody other than the user to access that data.
Learn more about this topic on The Guardian website.
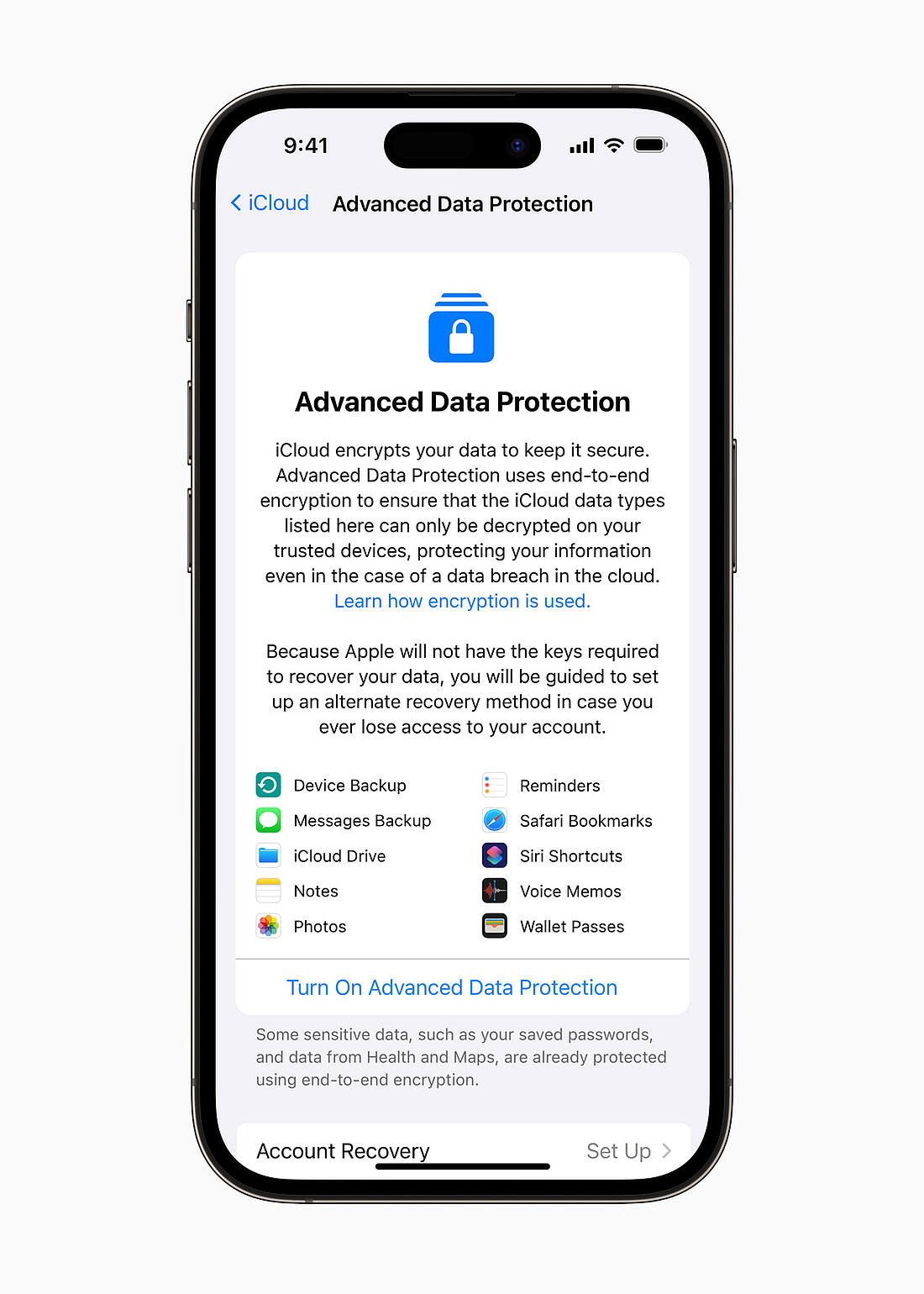
How to Secure User Data with Apple
End-to-end encryption of customer data stored on iCloud, or "advanced data protection for iCloud", will first be made available to a selected group of test users before being made publicly available in the US by the end of the year and internationally in 2023, according to Apple.
With the new service, data like notes, images, and iCloud-backed messages will all be completely protected.
Users will have to freely opt into the functionality, and the change will not apply to all data - email, contacts, and calendar entries will not be encrypted. The device will hold the encryption key or the code needed to access that secure data.
This implies that if a user who chooses to enable this protection loses access to their account, they will be responsible for utilizing their key to reclaim it - since Apple will no longer hold the encryption keys in iCloud.
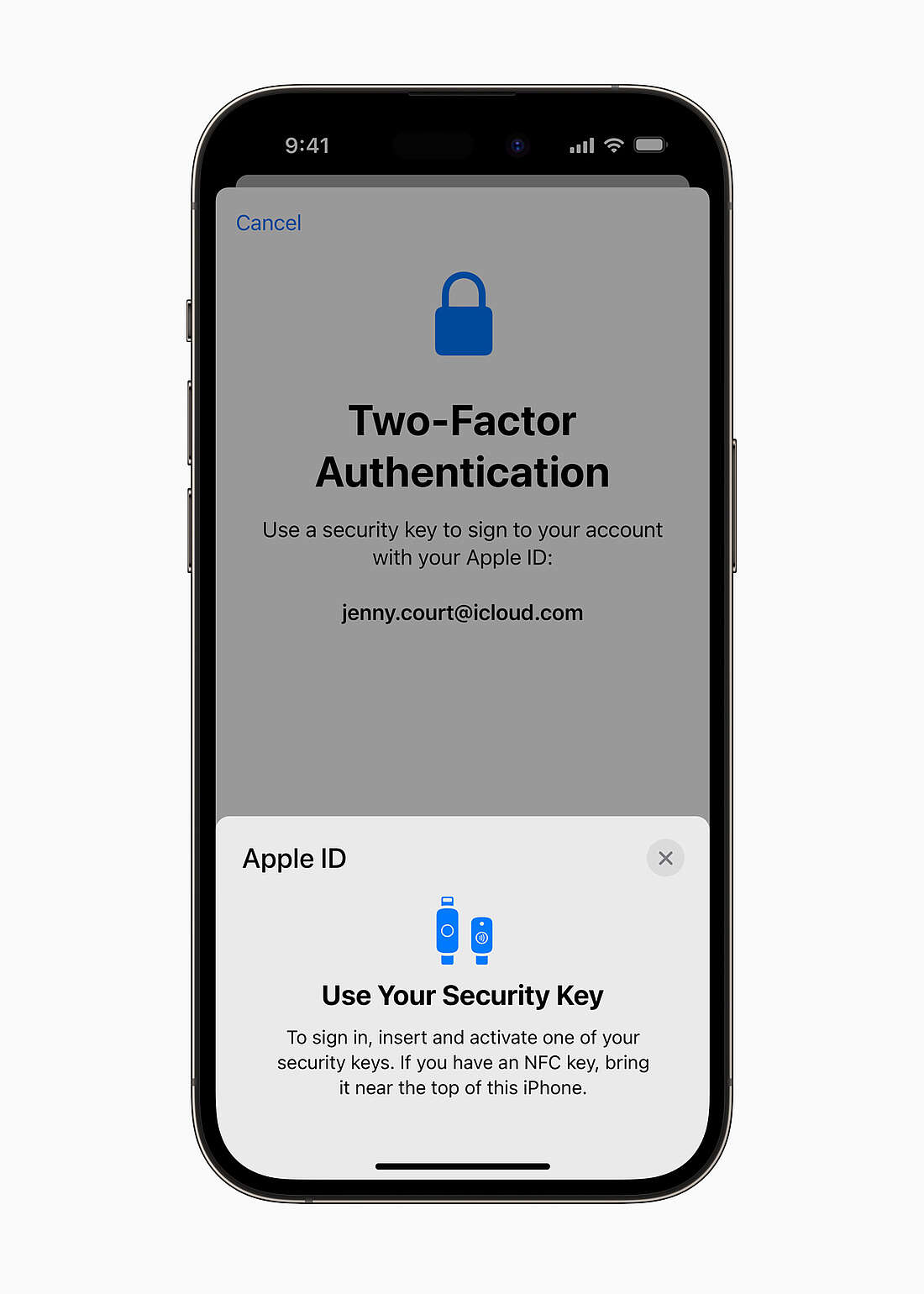
Moreover, Apple aims to implement a physical security key mechanism for users signing into their iCloud accounts on any new device, in addition to iCloud data protection. It serves as a hardware-based method for two-factor authentication.
In order to prove their identity while signing into their iCloud account on a new device, users who choose to use this extra level of security must insert a physical security key into the phones' charging port.
However, customers who decide to use this to secure their iCloud accounts are in charge of keeping track of those security keys, which include the primary key and a backup.
Last but not least, the business is introducing a code system that enables users to confirm that their communications are sent to the appropriate destination and are not being tampered with by hackers.
In Apple's scenario, two users of the system will be able to share their individual codes, and their devices will automatically determine whether a third user has joined the chat using a different code.
If a highly skilled opponent, such as a state-sponsored attacker, ever succeeds in compromising cloud servers and inserting their own device to secretly listen to a conversation on these encrypted communications, automatic alerts will appear in discussions between users who have enabled this verification function.
Concerns About Apple’s Data Protection Initiatives
Despite all of this, privacy activists such as Albert Fox Cahn, the creator of the Surveillance Technology Oversight Project, assert that these modifications may have a more immediate impact on the kinds of user data that law enforcement and governmental organizations can obtain from Apple.
“This type of protection is most valuable in protecting against not cyber criminals, but people who are abusing government power to force the company to hand over data,” Albert Fox Cahn said. “Apple has long been in the position where it’s had to be the long arm of the police for years. Their law enforcement manual shows dozens of ways that they can help with investigations and now for people who opt into the protection [feature], there will be a safeguard going forward.”
That might be a problem for government organizations trying to protect people's information for use in their investigations. Regarding whether it has discussed the adjustments with the government or law enforcement organizations, Apple declined to comment.
However, the FBI has already voiced its displeasure with the amendments that would prevent the agency from accessing user data. The FBI expressed its worry about Apple's decision to encrypt all iCloud content in a statement to the Washington Post, adding that the organization needed a backdoor or alternative method of accessing such data.
“This hinders our ability to protect the American people from criminal acts ranging from cyber-attacks and violence against children to drug trafficking, organized crime and terrorism,” the FBI said. “In this age of cybersecurity and demands for ‘security by design’, the FBI and law enforcement partners need ‘lawful access by design’.”
Apple unveiled last year a system to scan for unlawful content, such as child sex abuse materials, using a convoluted approach that would still permit Apple to encrypt user images on its servers, apparently in an effort to placate law enforcement.
Privacy activists rejected the idea, claiming that it would essentially give Apple access to peoples' hard drives.
So what’s it gonna be this time? Will these new initiatives be accepted by privacy defenders?
Share article
Get Started for Free
Gain World-Class Insights & Offer Innovative Privacy & Security

You might also like
Privacy Advocates Fine Clubhouse Talk App $2.1 Million 07 December 2022 - by Simon Coulthard
07 December 2022 - by Simon Coulthard
WhatsApp Data Breach of 487 Million Users 29 November 2022 - by Simon Coulthard
29 November 2022 - by Simon Coulthard