- Why Us?
- Features
White Label
For SaaS Platforms & Agencies
Provide our complete analytics suite to your clients, directly within your own interface and with your/their own branding. Discover Analytics-as-a-Service and White Label Analytics. Great benefit, minimal effort.
- Pricing
- White Label
- Success Stories
- ResourcesGetting Started
CONTENTS
- Compliance Audit Definition
- Types of Compliance Audits
- Compliance Audit Example
- Internal Audits vs. Compliance Audits
- Types of Compliance Regulations
- Seven Steps of the Compliance Audit Process
- How a Privacy-First Approach Simplifies Compliance Audits
- FAQ for Compliance Audit
- What Is a Compliance Audit?
- Why Are Compliance Audits Important?
- Who Needs a Compliance Audit?
What Is a Compliance Audit? Key Steps & Examples

Did you know that while 60% of executives believe their business is investing enough time and resources in compliance, only 31% of consumers agree?
That’s according to a consumer intelligence survey from PwC, the world’s largest professional services network. This gap presents a valuable opportunity to improve compliance efforts and build trust with customers.
Compliance audits play a crucial role in closing this gap, and this blog will guide you through what you need to know.
Just below, you’ll find the compliance audit definition.
But keep reading to explore the different types of compliance audits, how they differ from internal audits, and the key stages of the compliance audit process.
Compliance Audit Definition
→ The “Let’s Not Get Fined” Checkup
A compliance audit is a systematic examination of a business’s adherence to regulatory obligations.
Otherwise known as a regulatory compliance audit, it can encompass various aspects of the organization’s operations, including data protection, environmental sustainability, health and safety, labor and employment, and IT systems.
The purpose of a compliance audit is:
→ to ensure that internal systems are in place to meet regulatory expectations, and
→ that these systems can be demonstrated during a government or regulatory audit.
Furthermore, compliance auditing help verify that internal policies, systems, and processes are being consistently followed by employees.
Think of compliance audits as that mandatory “let’s not get fined” checkup every business should conduct regularly.
These regulatory audits serve as an effective means to identify compliance gaps, reduce risks, and issues that could lead to problems down the line.
This extends to the compliance of third parties, which 48% of businesses find challenging to assess (MetricStream).
Work to at least build a yearly compliance audit strategy so that you can proactively address compliance issues before they escalate.
Done well, these audits will help to avoid costly penalties and increase ESG ratings while maintaining trust with customers and stakeholders.
Types of Compliance Audits

Compliance audits are normally categorized based on their area of focus.
Here are some key types:
- Privacy Compliance Audits: Data privacy is a key business consideration and these audits assess an organization’s adherence to data protection laws and regulations, ensuring that personal information is collected, processed, and stored in accordance with legal requirements like GDPR and CCPA.
- IT Compliance Audits: Evaluate the effectiveness of IT security controls, data management practices, and data security measures to ensure compliance with relevant regulations, focusing on safeguarding sensitive information against breaches and unauthorized access.
- HR Compliance Audits: Evaluate human resource policies and practices to ensure they align with employment laws and regulations, including equal opportunity, safety, and wage compliance.
- Contract Compliance Audits: Review adherence to contractual obligations and terms, ensuring that all parties fulfill their commitments and comply with relevant laws.
- Social Compliance Audits: Focus on ethical practices within the supply chain, examining labor conditions, fair wages, and environmental impact to ensure adherence to social responsibility standards.
- Environmental Compliance Audits: Assess an organization’s adherence to environmental laws and regulations, focusing on eco-friendly marketing, sustainability practices, and waste management.
- Health Compliance Audits: Evaluate compliance with health regulations, ensuring that healthcare providers meet standards for patient care and data protection.
By understanding the different types of compliance audits, organizations can effectively target their efforts and enhance their overall compliance posture.
Compliance Audit Example
Since it would be legally questionable to delve into a real-world compliance audit example, let’s consider Tyrell Corporation, a fictional cloud storage company that recently conducted an audit to assess its compliance with GDPR.
The audit kicked off with analysis of their privacy policy, which revealed outdated language that lacked the clarity on data collection practices expected by this legislation. This promoted them to create a better privacy policy that improved the transparency of communication about data practices and user rights.
The corporation then conducted interviews with the Data Protection Officer (DPO) and other key staff. This revealed a previously hidden gap in employee knowledge regarding current compliance requirements, motivating the company to set up training sessions around data privacy best practices.
Further investigation revealed that the Tyrell Corporation needed to improve their consent management processes. Their customers were struggling to understand exactly what they were consenting to, meaning that they needed a better framework. The audit team recommended a number of changes that would make the consent process more translparent and user-friendly.
They also analyzed account login credentials, finding that too many employees had access to sensitive data - a position that increased the likelihood of a data breach.
Following the audit, the company created an action plan for addressing the issues they discovered, and they also scheduled follow-up audits to track the effectiveness of these measures.
Internal Audits vs. Compliance Audits
While compliance audits can be conducted internally or by external auditors, “internal audits” is actually a separate category that is distinguishable in key ways.
Each serves a unique purpose and has distinct objectives, focus areas, and scopes.
Here’s a breakdown:
Internal Audits | Compliance Audits | |
Purpose | Evaluate the effectiveness of internal controls, risk management, and governance processes. They help ensure operational efficiency, and identify areas to improve. | Evaluate adherence to external regulations, laws, or internal policies related to specific areas, such as data privacy, environmental standards, or financial regulations. |
Scope | Broad and encompasses various aspects of the organization, including financial processes, operational efficiency, IT systems, and compliance with laws and regulations. | Narrower, specifically targeting compliance with relevant laws and regulations. For instance, a privacy compliance audit would assess how well the organization complies with GDPR or CCPA. |
Responsibility | Typically carried out by an internal audit team or department that reports directly to senior management or the board of directors. | Can be conducted internally, but are often performed by external auditors or regulatory bodies to provide an unbiased assessment of compliance status. |
Frequency | Usually conducted on a regular basis (e.g., quarterly or annually) as part of a comprehensive internal control framework. | Frequency depends on regulatory requirements or business needs, and may be conducted more often in high-risk areas. |
In summary, while both internal audits and compliance audits aim to improve organizational performance and mitigate risks, they differ in focus, scope, and how they are conducted.
Compliance audits can certainly be performed internally, but they typically hone in on regulatory adherence rather than the broader internal controls assessed in internal audits.
Types of Compliance Regulations
Compliance regulations can vary significantly depending on the industry and geographic location. Here are some common types:
- Data Protection Regulations: CCPA and GDPR compliance audits enable businesses to verify whether how they collect, store, and use personal data meets key privacy requirements.
- Financial Regulations: Standards set by regulatory bodies like the SEC to ensure transparency and accountability in financial reporting.
- Health Regulations: Compliance requirements such as HIPAA that protect patient information and ensure safe healthcare practices.
- Environmental Regulations: Laws that mandate environmental protection and sustainability measures, often enforced by agencies like the EPA.
- Labor Regulations: Employment laws that protect workers' rights, ensuring fair treatment, safety, and wage compliance.
Understanding these regulations is essential for businesses to operate lawfully and ethically.
Seven Steps of the Compliance Audit Process
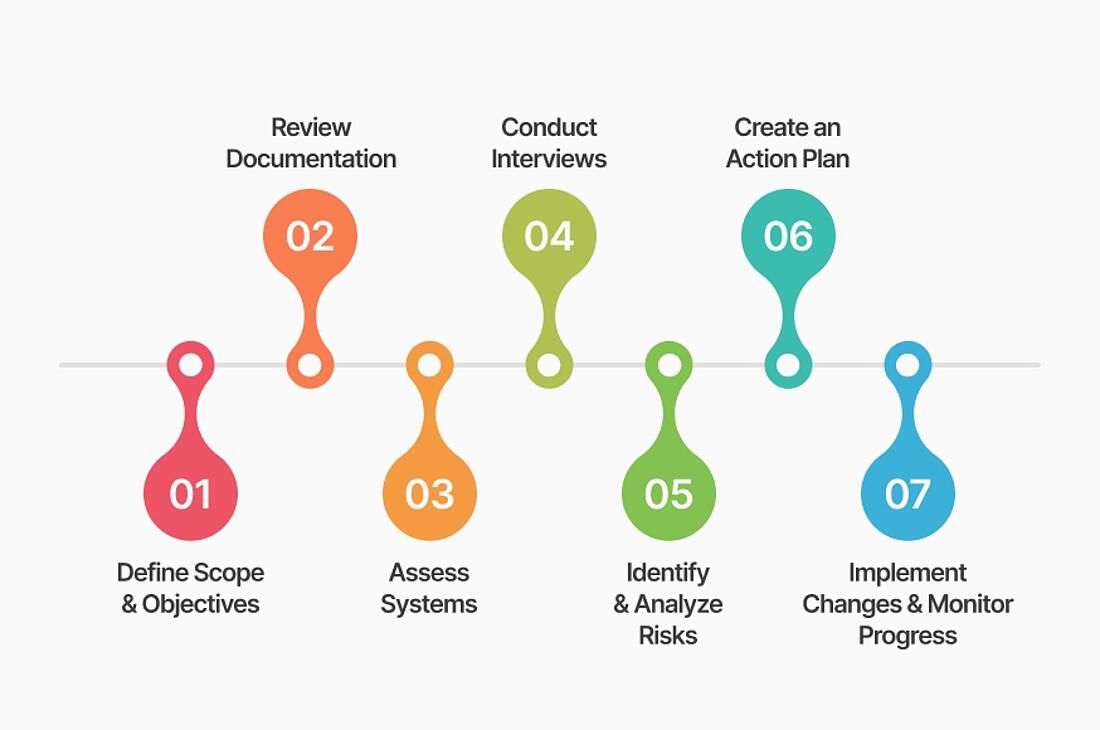
A compliance audit examines a business’s systems and processes to identify potential risks and ensure adherence to privacy regulations. While they are usually conducted by an independent third party, here’s a breakdown of the essential stages for businesses performing an in-house audit:
- Define Audit Scope and Objectives
Identify the regulations that impact your business, including data privacy and industry-specific laws. Clearly define the objectives of the audit to focus efforts on critical areas. For example, if your business processes sensitive customer information, prioritize compliance with regulations like GDPR or CCPA. - Gather and Review Company Documentation
Collect all internal files and protocols that your operations are built around, including privacy policies, credentials, data handling processes, and documentation related to third-party relationships. Organize these materials systematically to make it easier to review compliance practices. Utilize checklists to ensure you cover all necessary documents, and note any inconsistencies that require clarification. - Assess Systems
Evaluate how your systems collect, process, and store information across the full data lifecycle. This includes reviewing software, databases, and any technology used in data handling. Conduct a system audit to identify any vulnerabilities or outdated technology that could expose your business to risks. For example, ensure that encryption protocols are in place for sensitive data and that access controls limit data exposure to authorized personnel only. - Conduct Interviews
Meet with key personnel, such as department heads, data protection officers, and IT staff, to understand their data practices. This dialogue helps uncover how data flows within your business, ensuring procedures align with privacy requirements. Prepare questions in advance that focus on data handling practices, incident response, and awareness of compliance responsibilities. - Identify and Analyze Risks
Pinpoint potential issues, such as inadequate data security, access overreach, or weak consent management. Use a risk assessment matrix to categorize and prioritize identified risks based on their potential impact and likelihood. This structured approach will help you focus on the most critical vulnerabilities that need immediate attention. - Create an Action Plan
Develop a strategy to address any identified problems. Your action plan should include specific steps to mitigate risks, assign responsibilities, and set deadlines for implementation. For example, if you discover gaps in employee training on data privacy, include a plan to enhance training programs and set up regular refresher courses. Additionally, ensure that you allocate resources appropriately to support these initiatives. - Implement Changes and Monitor Progress
Put your action plan into effect and monitor its success. Establish key performance indicators (KPIs) to measure the effectiveness of your changes. Schedule regular check-ins to review progress and adjust the plan as necessary. For instance, if a new data management tool is implemented, gather feedback from users to assess its effectiveness and identify areas for improvement.
Remember to conduct these at least once a year, and to keep a record of compliance audit reports.
This will not only help maintain compliance with privacy regulations but also enable you to proactively identify and mitigate potential risks as your business grows, as employees turn over, and as laws evolve.
To help, you could even consider scheduling audits semi-annually or quarterly for high-risk areas or after significant changes in operations, such as the introduction of new technologies or processes.
Simply put, the compliance audit process is a great way to build a culture of compliance within your organization, and to hammer home the responsibility that all employees have to carry out their work with good data discipline.
How a Privacy-First Approach Simplifies Compliance Audits
Prioritizing privacy when selecting software can drastically reduce the burden of compliance audits. This is particularly true of website analytics, which is often a focal point in audits due to the volume of customer data collected.
TWIPLA is an ideal choice.
We’re a privacy-perfect website intelligence platform built around privacy-by-design principles, which includes:
- Data Minimization: We only collect the data necessary for insights, ensuring no unnecessary information is processed.
- Data Anonymization: Our data collection processes can be easily calibrated to eliminate all personally identifiable information (PII), ensuring that individuals cannot be identified.
- 100% Data Ownership: Clients maintain full control over their data, with easy consent management and the ability to modify or delete information at any time.
- Robust Data Security: Advanced encryption and security protocols protect sensitive data from unauthorized access.
- Consentless Tracking: TWIPLA’s consentless tracking ensures compliance without the need for cookie banners, streamlining the user experience while adhering to privacy regulations.
- Data Transparency: We provide clear visibility into how data is collected and used, empowering users and businesses alike to understand and manage their data responsibly.
These features mean our platform can be used in compliance with all global data protection laws by default, without creating any compliance responsibilities. This makes TWIPLA a powerful tool for simplifying compliance and reducing the manual workload during audits.
But it’s equally important to apply this privacy-first mindset to all your software choices, from customer relationship management systems to cloud storage, to build a robust compliance framework.
By embedding privacy across all your operations, you not only simplify the audit process but also foster a proactive culture of data protection, making it easier to maintain regulatory standards across the board. With the right tools in place, audits become less about finding and fixing issues and more about demonstrating that your systems are already compliant.
FAQ for Compliance Audit
What Is a Compliance Audit?
A compliance audit can be done in house, or by an independent third party. It evaluates a business’ operational adherence to both its own internal policies and legal regulations, particularly those related to data protection, privacy, and industry-specific standards.
Why Are Compliance Audits Important?
Compliance audits are important because they allow businesses to identify risks before they escalate, ensure regulatory compliance, and safeguard sensitive data. This ultimately helps them to avoid penalties for breaches or non-compliance, and maintain customer trust.
Who Needs a Compliance Audit?
Data management is a legal requirement and any business that collects, processes, or stores personal information should carry out a compliance audit at least once per year to assess their internal processes and compliance with data privacy laws.
Share article
Get Started for Free
Gain World-Class Insights & Offer Innovative Privacy & Security









